How does an access control system work?
You rely on us to be the access control experts.
But have you ever wondered how your building’s access control system works? In this article, we’ll explain the basic features of most access control systems.
Purpose
The purpose of any access control system is to restrict access to specific doors to qualified personnel, to control when those doors are accessed, and to view historical logs of when certain areas were access and by whom.

Credential (Card, Fob, Tag, Etc.)
Though it may look like a piece of plastic, each credential contains an electronic coil and a unique ID.
Credentials do not contain batteries and have very long life cycles. Instead of batteries, credentials have coils inside of them that energize when presented to an energized coil of the same resonant frequency.

Card Reader
The card reader also has an electronic coil inside it. This coil emits a continuous low-energy pulse several times a second. When a key card, fob, or tag credential comes in close proximity to the card reader, the electronic coil in the card reader energizes the electronic coil in the credential, and the credential transmits its identification number to the reader.

Door Controller
Once the card reader reads a presented credential, it sends the ID of the credential to the door controller. In the door controller resides a copy of the user database, which includes a full list of names and credentials and the access permissions that each person has. When the door controller receives a credential, it decides allow or deny access.

Lock
The door controller has lock outputs or relays that activate an external power source to supply voltage to the lock outputs. Two categories of lock exist: fail-safe and fail-secure. Fail-safe locks will receive voltage to unlock, and fail-secure locks will unlock upon loss of voltage. It’s not uncommon for buildings to have a combination of fail-safe and fail-secure locks. Fail-safe locks are commonly found in building stairwells due to code requirements. Any electromagnetic lock will release upon loss of voltage and they would therefore also be considered “fail-safe”.
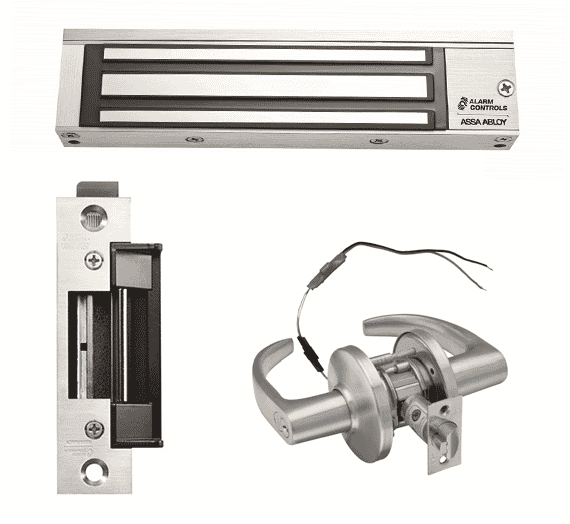
Door Position Sensor
A “door contact” is the most common form of door position sensor. The contact is installed in or on the door frame, and a magnet is installed in or on the door so that when the door is closed, the magnet comes very close to the contact. The contact contains a “reed switch,” which changes state when a magnet is present. This reed switch wires back to the door controller, and the door controller can know in real time whether the door is open or closed.

Request-to-Exit Sensor ("REX")
A REX is installed on the opposite side of the door from the card reader. While the card reader tells the door controller that someone is trying to get in, the REX tells the door controller that someone is trying to leave.
The most common type of REX is a motion detector mounted above the door on the wall or the ceiling. When the REX detects motion, it will signal an exit event to the door controller. If the door has mechanical exit hardware, the REX is purely for event signaling and preventing “door forced open” events from occurring on the system. In the case of an electromagnetic lock, where the holding force prevents opening the door from either side, the door controller will be programmed to unlock the door upon a REX event.

Secure Database
The door controller receives its database information from an externally managed database. The database contains the latest information of cardholders, access levels, schedules, and any other site-specific information. The database is often in constant communication with the door controllers and pushes changes down to these controllers automatically any time a change is made. Advanced databases such as the ones running on our Hattrix servers run multiple backups daily, run in a Tier 3 server environment, and provide unparalleled connective uptime. These servers are also capable of emailing customers upon specific system or user events.
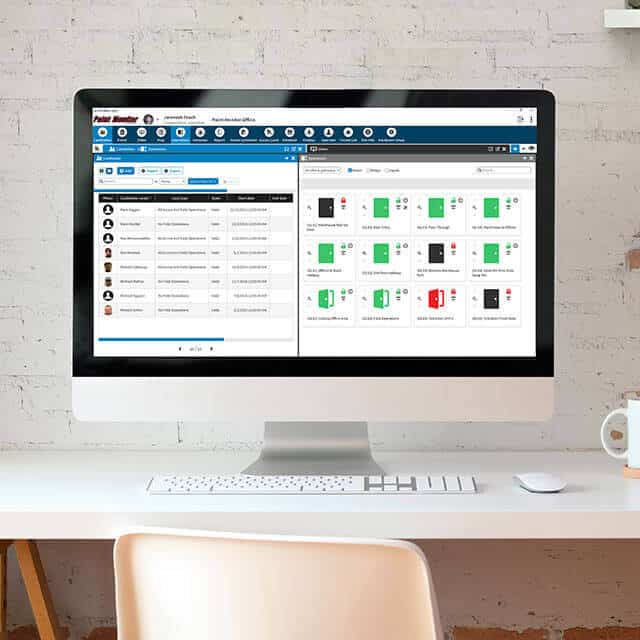
User Portal
The portal is where administrators add, edit, and delete cardholders, access levels, schedules, holidays, etc. It is also where doors can be manually locked and unlocked and event reports generated.
On legacy systems, administrators may program their system through the primary database software itself. Modern portals, such as the one available on our Hattrix platform, give administrators access to their databases in several ways. They allow programming through computers, smartphones, and tablets. User workspaces can also be fine-tuned to limit the amount of control that particular users have.
Where does your building fit in?
No two access control systems are exactly the same. Point Monitor has a long history of custom applications and solutions for a wide variety of industries. Our team would love to help you design a tailor-made access control system for your building!